Windows Buffer Overflows – 32 Bit.
Get the Buffer Overflow in 11 Steps.
I. Install the immunity debugger on source machine.
II. Find the Vulnerable parameter in the victim application by crashing it. Providing high volume of input.
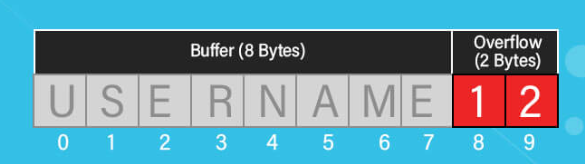
III. Identify the location [That 4 Bytes] where crash is happening by Fuzzing the application.
IV. Get the exact EIP pointer with the help of immunity debugger.
V. Remove the BAD Characters. [\x00 -default one]
VI. Use the command !mona modules find a file with no memory protection mechanisms.
[command: !mona jmp -r esp -m “file name”]
VII. Get the first return address value and overwrite the EIP with the above found address.
VIII. Generate the shell code to exploit. We can use msfvenum to generate don’t forget to mention the bad characters.
IX. Build the payload [User Input + Return Address + “\x90″*32 (NOP slide). + Payload]
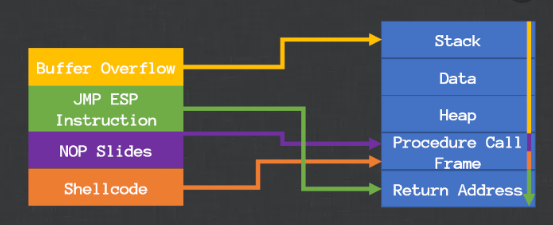
X. Setup the listener on the same port which configured in MSFVENUM.
XI. Once you provide this framed input, you’ll receive the reverse shell from the windows machine if everything in its place.
Download : https://debugger.immunityinc.com
Get the Buffer Overflow in 11 Steps. I. Install the immunity debugger on source machine. II. Find the Vulnerable parameter in the victim application by crashing it. Providing high volume of input. III. Identify the location [That 4 Bytes] where crash is happening by Fuzzing the application. IV. Get the exact EIP pointer with the…