Access the Inaccessible – SSH Port Forwarding
SSH port forwarding, also known as SSH tunneling, is a technique that enables the forwarding of network connections from one computer to another through an SSH server. It establishes an encrypted channel between the local and remote hosts, ensuring the confidentiality and integrity of the transmitted data. This feature makes SSH port forwarding an excellent choice for scenarios where secure access to remote services or protection of sensitive information is required.
In cases where certain services or websites are blocked or restricted, SSH port forwarding can provide a way to bypass such restrictions by tunneling the traffic through an SSH connection to a server located in an unrestricted network.

There are three main types of SSH port forwarding:
Local port forwarding
Local port forwarding allows you to redirect connections from the local machine to a remote server or service via an SSH connection. This is useful when you want to access a service on a remote server that is not directly accessible from your local network.
ssh -L <local_port>:<destination_host>:<destination_port> <username>@<remote_host><local_port>: Local port number to use for port forwarding. This port will listen on your local machine. <destination_host>: Hostname or IP address of the destination host you want to reach. <destination_port>: Specify the port on the destination host to which you want to forward the traffic.<username>: Replace this with your username on the remote host. <remote_host>: Provide the hostname or IP address of the remote host you want to connect to.
To set up local port forwarding from your local machine’s port 8888 to a destination host with IP address 192.168.1.200 and port 80, and your username on the remote host is user123, and the remote host’s IP address is 192.168.1.100. The command would be:
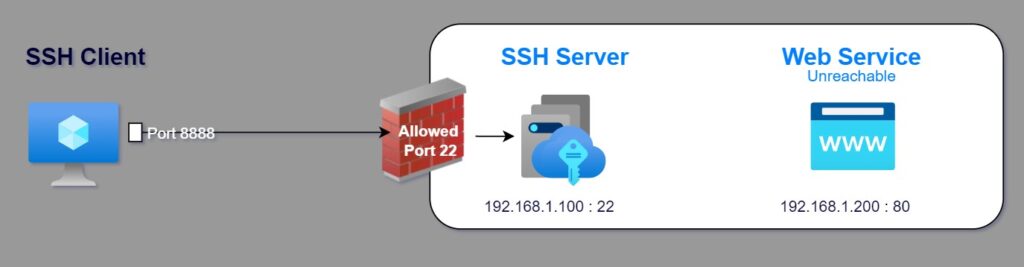
ssh -L 8888:192.168.1.200:80 [email protected]
After executing this command and successfully authenticating with your password, SSH will start listening on the local port 8080. Any traffic sent to localhost:8888 on your local machine will be forwarded to the destination host (192.168.1.200:80 in this example). This allows you to access the destination host’s service (e.g., a web server) through your local machine’s port 8888.
Remote port forwarding
Remote port forwarding enables you to redirect connections from a remote server to a local machine. It allows others to access services running on your local machine securely through the SSH tunnel.
ssh -R <remote_port>:<destination_host>:<destination_port> <username>@<remote_host><remote_port>:Remote port on the remote host use for port forwarding. It will listen on the remote host.<destination_host>: Destination host that you want to reach through the port forwarding.<destination_port>: Specify the port on the destination host to which you want to forward the traffic.<username>: Replace this with your username on the remote host. <remote_host>: Provide the hostname or IP address of the remote host you want to connect to.
You want to set up remote port forwarding from a remote machine’s port 8080 to a destination host with IP address 192.168.1.200 and port 80, and your username on the remote host is user123, and the remote host’s IP address is 192.168.1.100. The command would be:
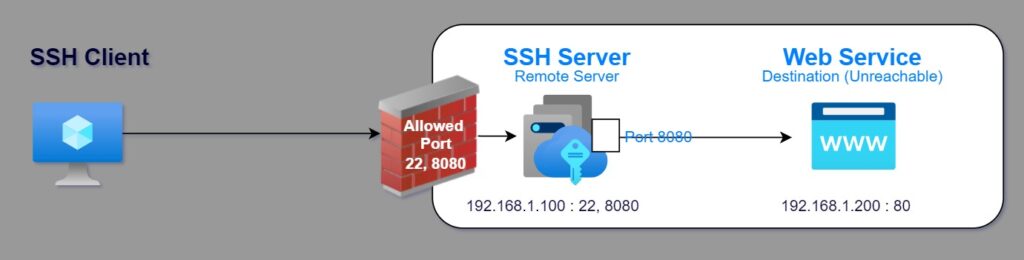
ssh -R 8080:192.168.1.200:80 [email protected]
After executing this command and successfully authenticating with your password, SSH will start listening on the remote port 8080 on the remote host. Any traffic sent to localhost:8080 on the remote host will be forwarded to the destination host (192.168.1.200:80 in this example). This allows you to access the destination host’s service (e.g., a web server) through the remote host’s port 8080.
Dynamic port forwarding
Dynamic port forwarding, also known as SOCKS proxy, is a powerful feature that allows you to create a secure tunnel for all network traffic originating from your local machine. It can be used as a proxy server, enabling you to browse the internet securely or access services on remote networks.
ssh -D <local_port> <username>@<remote_host><local_port>: Local port to use for dynamic port forwarding. It will be used as a SOCKS proxy. <username>: Replace this with your username on the remote host. <remote_host>: Provide the hostname or IP address of the remote host you want to connect to.
Let’s say you want to set up dynamic port forwarding with a local port 8888, and your username on the remote host is user123, and the remote host’s IP address is 192.168.1.100. The command would be:
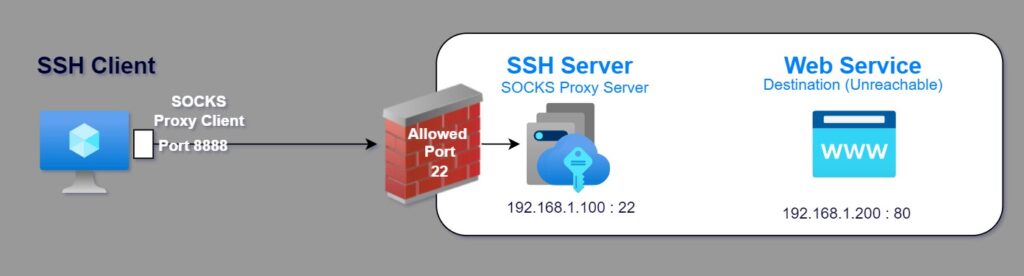
ssh -D 8888 [email protected]
After executing this command and successfully authenticating with your password, SSH will start listening on the local port 8888, acting as a SOCKS proxy client. You can configure your applications to use this local port as a proxy client to tunnel their traffic through the remote host [SOCKS proxy server] securely.
Conclusion:
SSH port forwarding is a powerful networking tool that enables secure and encrypted communication between local and remote systems. Its ability to establish tunnels for various types of network connections offers flexibility and versatility in a wide range of scenarios. Whether it’s for secure remote access, encrypted file transfer, bypassing restrictions, or local development, SSH port forwarding remains a go-to solution for network professionals seeking a reliable and secure way to establish connections over untrusted networks.
SSH port forwarding, also known as SSH tunneling, is a technique that enables the forwarding of network connections from one computer to another through an SSH server. It establishes an encrypted channel between the local and remote hosts, ensuring the confidentiality and integrity of the transmitted data. This feature makes SSH port forwarding an excellent…