EWU Gates – Are you safe?
Cyber Attacks, you started hearing these words on a daily basis in news and social media. Protecting yourself and your organization from cyber-attacks can become a big challenge.
So, come up with a few basic prevention methods for Organizations and Individuals that may keep you and your data safe.
Before preventing, you need to understand how the attacks happen and what are the ways attackers come in. These are the way most hackers choose to come inside your systems:
WEB
USB
Malware, phishing and online frauds: all these attacks delivery options would be any of these. Moreover Command and Control, man-in-the-middle use the web. Passwords, Personal information and Organization’s confidential information are compromised via emails. Critical VIRUS and WARMS passes through unblocked USB, that leads to making the system or environment down.
Let’s talk about email. Email is one of the easiest ways to deliver a malicious website [URL] or Attachment. Sending Spam emails and forcing you to reply is one of the reconnaissance methods. Organizations are protecting these kinds of emails using various tools like email secure gateway, sandbox and exchange. But sometimes attackers are smart enough to overcome these stumbling blocks.
So the Key is to educate the user. If the users are aware of what spam, phishing and malicious attachments are, they can protect themselves from these attacks. Moreover, not only security analysts, each and every one has to know how to analyse the email. Mostly if we receive the email from an unknown sender, we will get a little curious to know about what is inside, then clicking on the link after that opens the attachment. BOOM!!! That’s it. You’re compromised. Then from the effects of the attack, you can learn how to prevent being compromised with ransomware. You almost lost all the files. Your mind’s voice may say, ‘Why did I open the attachment?’ Yes!! Opening the attachment from unknown senders sometimes puts you in this state.
Spoofing is another danger. Most of the time, Organizations receive emails spoofing Microsoft. Individuals can also receive emails spoofing Amazon and other shopping sites.
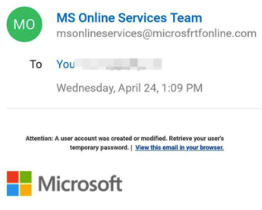
When you receive emails like this, the first thing you need to do is verify the email address of the sender. You need to verify the Name and Domain very carefully. Then, the body of the email which makes you curious, then waits. Don’t open the attachment and don’t click the link until you’re 100% sure it is not a spam or malicious email. The URL’s in the email force you to enter credentials of google, Facebook or an Organization. By verifying the URL of the login page, you can identify the spoofing. How to identify if it is not a malicious email? We will discuss this in further blogs.
WEB
The Web is an ocean. The diagram below explains that very well. The tip of the iceberg is nothing when you compare the depth of it. This is applicable for the Web too.
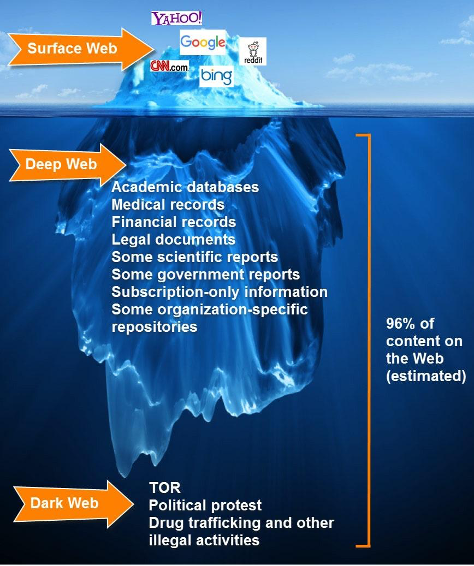
You may receive SMS’ or WhatsApp forward messages, offering 1TB hard disk for 1$. Your immediate action will be clicking on the link. You never think about what will happen if it happens to be a malicious URL. That may lead the attacker to get information about your device and personal information. Sometimes downloading a few malicious files in temp and waiting for the time, like a time bomb, then Blast. Attackers get a command and control on your device.
How to protect ourselves from the Web. Minimum we are accessing 10 websites per day. So, what websites we are accessing we need to be aware of it. Modern browsers started doing the jobs like identifying the malicious websites and warning you. Antivirus will also help sometimes. Identify the Deep and Dark web and avoid surfing over there. Surfing there is like grabbing a tiger by the tail.
Organizations spend millions of dollars to protect the environment from the web. Proxy, Nextgen Firewalls, Sandboxing, Threat intel etc.. Even though newly created and uncategorized or wrongly categorized URLs can harm your organizations. Creating user profiles in proxy and categorizing the users wisely will protect 50%.
Ultimately keep an eye on the URL bar and check the spellings.
USB
USB attacks need physical interactions. USB attacks are straightforward. All you need is just connect the removable media with the system. Remaining job will do. No more interaction required. Autorun.inf file defines the files needed to execute. Antivirus can help 80% protecting from the removable media if you’re not disable it.
Few Organizations block the USB at the Operating System level. Most of the organizations block it with Endpoint solutions like antivirus. But I have noticed mid-level or small organizations never block the USB. That is really dangerous. Even the banks having domain PCs in the branches, sometimes they failed to verify the Antivirus enabled checks. That allows the users to connect the USB, unfortunately attackers too. Many real incidents occurred in this manner. So Organizations need to give each and every PC. Spending millions at perimeter level and not caring about the endpoints is not a wise practice.
For Individuals, Don’t connect the USB got from unknown sources. Even if you connect, remove your computer from the network and connect. Verify your antivirus status before connecting. Don’t install the software if you’re not aware of it. Before installing the software verify the HASH value of the software from the original source. Scan it in a regular interval.
Conclusion
Protecting ourselves from attackers becomes a big challenge. But identifying the way coming in and protecting it will help to keep us safe.
Don’t entertain with Unknown sources. Verify the known sources.
Cyber Attacks, you started hearing these words on a daily basis in news and social media. Protecting yourself and your organization from cyber-attacks can become a big challenge. So, come up with a few basic prevention methods for Organizations and Individuals that may keep you and your data safe. Before preventing, you need to understand…
Too much of lecture