How Organizations Detect the Cyber Attacks?
Organizations running with more than 1000 employees, need to have big infrastructure. Organizations running with more than 100,000 employees need to have very big infrastructure. Providing security to this infrastructure is very challenging. When it comes to security, providing physical security is not enough. Organizations need to invest much more on cyber security. Multilayered security is required to secure the confidential data.
Imagine you have thousands of assets and one of those assets got compromised. Now, how could you identify the attack? Also, in the case of data leakage, how could you detect it?
Before answering these questions, you need to understand how organization protects themselves from the cyber security breaches.
Firewalls will be placed in perimeter level and internally. IPS, Web Application Firewalls, proxy, Antivirus, HIPS and other end point security tools helps them to protect the assets behind it. But we need to keep it in mind that these security devices are useless until it is configured properly. Configuring devices is human effort. In case any human error occurred, you can expect cyberattacks through those loopholes. That time, you need to detect them. Is that possible?
Yes! It is. There were SIEM playing the role similar to soldier watchtower. Let’s see how it is possible technically.
SIEM Tool
SIEM, stands for Security Information and Event Management. This SIEM tool is integrated with all devices, from perimeter routers to user mobiles. It is integrated with Network devices, security devices, Operating Systems, Databases, Applications and Active Directory too.
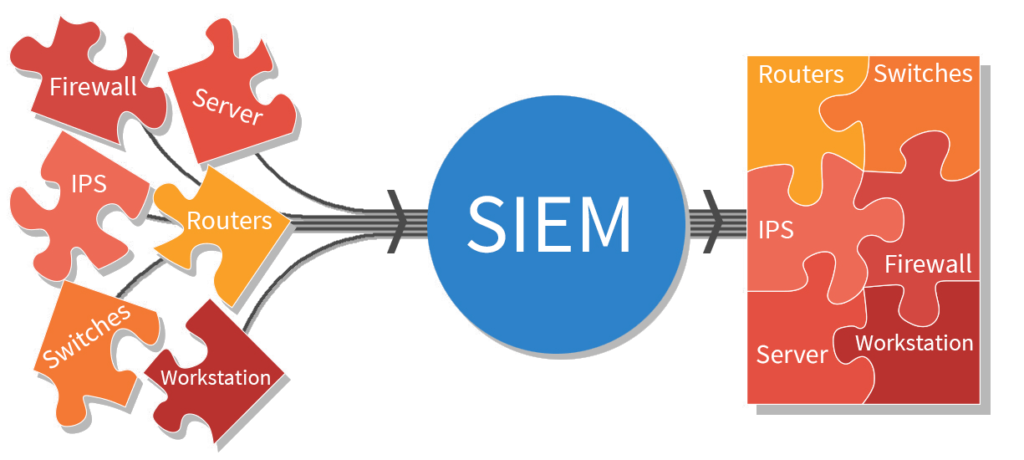
A system integrated with SIEM means it is successfully giving the logs to the SIEM tool. What kind of logs? Every system has variety of logs. For example, for Windows machines, most commonly, SIEM tool collects security, application and system logs. In firewall, we have traffic logs, configuration logs, system logs and more. But choosing the log type is the SIEM administrator’s call. The factors such as Sector, Organization and License decide the choosing of the log types.
So, If SIEM tool is collecting logs from all the devices. What is next?
The next step is processing the logs [Parsing and consolidating] and then storing the processed logs in the data base.
SIEM tool having the Use cases, Dashboards, Reports and search queries were created by administrator or users. Some of the SIEM tools process the use cases, Dashboards and queries before logs get stored into the data bases. Some of the SIEM tools process it after getting stored, into the database. Most commonly, these contents use queries similar to SQL.
For example, A use case defined to identify “10” Failed login Attempt from a Linux server [hostname: linux01] within 1 minute. Most probably, this scenario could be the attack.
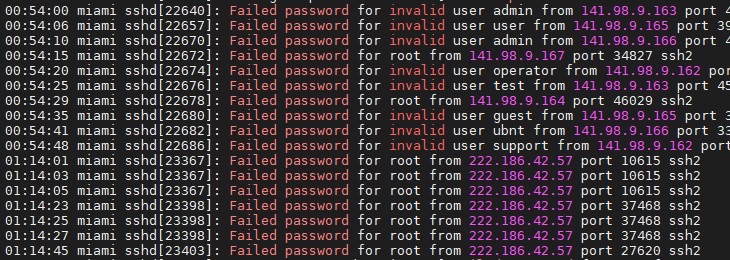
That will be defined as given below.
Hostname=”linux01″ AND name CONTAINS “Failed password”
And the aggregation part is defined as “10” events [Logs] in “1” minute.
As we said earlier, some of the SIEM tools monitor the logs with these conditions before storing into the database. Some of the SIEM tools use these conditions and search from the database.
Coming to important spot, suppose the above condition got matched, then what will happen?
Alert! it will alert to SOC team with defined information. What information are need to be in the alert, is defined by the administrator or the one who created the use case.
What is SOC? Security Operations Center which is running 24*7 with different levels [L1, L2 & L3] of Analysts. L1 is the first one who pick the alert. L2 is the one who takes action on the alert. L3 is the one who handles the critical incidents.

Generally, logs will get generated after the event occurred. Then it is received by SIEM. So SIEM is alerting after the attack? This question might arise in everyone’s mind. Yes! But not all the time. Attacks will not happen in a single stage. It has multiple processes like reconnaissance, delivery, exploit and etc. If we have a list of block listed IP, we can stop the attack while attackers are doing reconnaissance. If we have IOC listed domains, we can protect the system from Command and Control. Security devices also provide information about attacks to SIEM tool. Threat Intelligence feeds are very useful to identify the threats before it hurts.
There are frameworks like MITRE attack. It is a package contains Use cases, Dashboards and Reports. Just by importing them to our SIEM solution, we can make them effective in our network. This MITRE attack frameworks has pre-defined attackers’ tactics and techniques. This help us to protect the environment before it is gets compromised. Moreover, it assists to identify the lateral movements [Post attack activities].
At the end, how effectively use cases and SIEM tool is configured become important.
Conclusion:
SIEM solution is the backbone of the Security Operations Center. Based on how many devices were integrated and how many devices productively triggered alerts, we can detect the cyberattacks and protect on top of that. Alerted events can be false positive sometimes. Fine tuning will give hand to trigger the true positive events. SLA is the KEY. Taking action on true positive events in a quick manner can save millions and billions.
Organizations running with more than 1000 employees, need to have big infrastructure. Organizations running with more than 100,000 employees need to have very big infrastructure. Providing security to this infrastructure is very challenging. When it comes to security, providing physical security is not enough. Organizations need to invest much more on cyber security. Multilayered security…