IDOR – Do you know what I am doing ?
An application provides direct access to an object, such as a file or a database record, based on user-supplied input. This can allow an attacker to bypass the application’s access controls and access sensitive information or perform unauthorised actions it is called as an IDOR (Insecure Direct Object Reference) vulnerability.
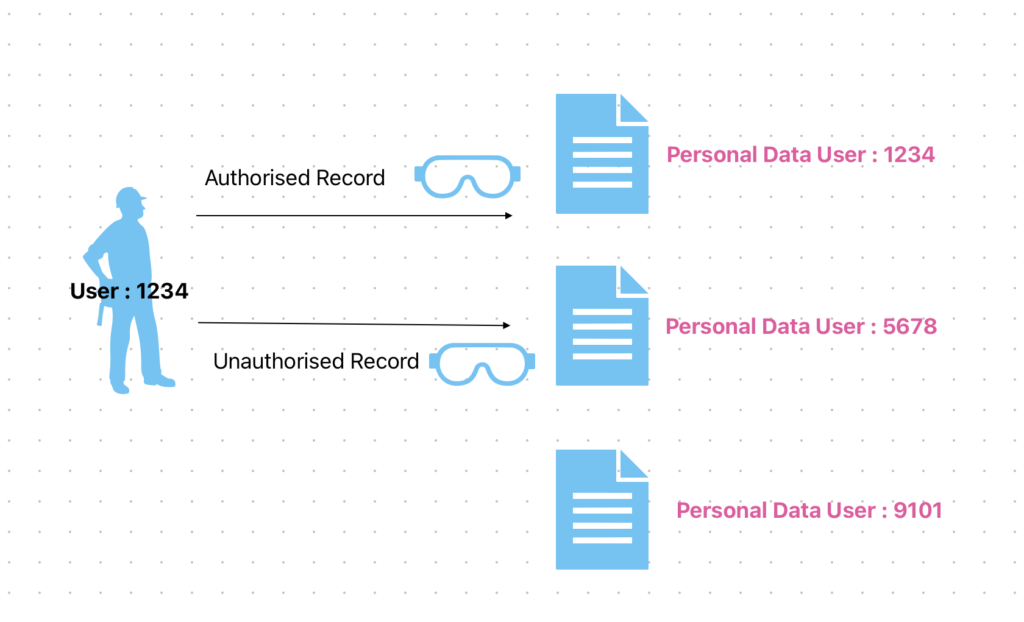
Attacker can manipulate the URL or form data to gain access to data that they should not be able to see.
An example of an IDOR vulnerability would be a website that allows users to view their account information by accessing a URL like “www.xyz.com/viewAccount.php?id=1234“. An attacker could simply change the “id” parameter in the URL to “5678” and view someone else’s account information.
It is also important for organizations to regularly test their applications for vulnerabilities, including IDOR vulnerabilities, by using automated tools or hiring a professional penetration testing company.
To prevent IDOR vulnerabilities, developers should ensure that all sensitive data is properly protected by implementing appropriate access controls encryption and authentication. This can be done by using a server-side script to validate that the user has the appropriate permissions to access the requested data, or by using a unique token or session ID to authenticate the user. Additionally, developers should also validate all user input to prevent malicious data from being passed through the application.
Overall, IDOR vulnerability is a serious security concern that can have significant consequences for both users and organizations. It is important for developers to be aware of the risks and take steps to prevent IDOR vulnerabilities in their applications.
An application provides direct access to an object, such as a file or a database record, based on user-supplied input. This can allow an attacker to bypass the application’s access controls and access sensitive information or perform unauthorised actions it is called as an IDOR (Insecure Direct Object Reference) vulnerability. Attacker can manipulate the URL…