SYSMON – Free EDR?
Protecting Endpoints are challenging. It has become more crucial after the COVID pandemic. Work from Home has made Cybersecurity more proactive from reactive. Endpoint detection and response (EDR) is providing security for user machines. It helps to protect Files, Web, and Removable media. But acquiring EDR is not easy for all firms. Giant institutions, they go with EDR. Besides, for small organizations it is more challenging due to financial and resource issues.

So, the free tool Microsoft Sysinternals Sysmon developed by Mark Russinovich helps to replace EDR for small-scale industries. The difference is EDR responds immediately whereas Sysmon only informs the analyst. But here everyone needs to know that bypassing EDR is possible in multiple ways for the attackers. Sysmon covers process, network, file, and registry related logs.
Examining Sysmon’s Effectiveness as an EDR Solution, Christian Vrescak’s paper says, “Sysmon may not offer visibility for every attacker technique, but this research has shown that most ATT&CK techniques are covered. With proper care and feeding, this solution can become a defender’s ace in the hole.”

Sysmon tool is available for Windows and Linux Machines; Windows having windows event viewer and Linux having syslog. Then why do we need Sysmon?
Windows event viewer and syslog are limited; Visibility is less. Sysmon produces more prominent levels of visibility on security related events.
Installation is simple and straight forward. Install the setup file and import the configuration file. The configuration file in XML includes what to monitor and what not to.
Let us see the Installation process.
Download the setup from the below sources:
Windows: https://download.sysinternals.com/files/Sysmon.zip
Linux: https://github.com/Sysinternals/SysmonForLinux
Follow the below steps to install. After that, send the logs to SIEM or Log management tools for Analysis.
Open CMD run as administrator.
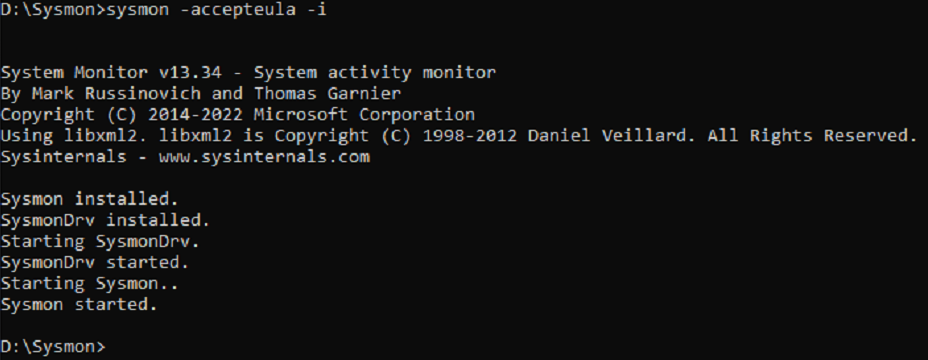
Go to the Directory where exe file is located. Type the command:
sysmon -accepteula -i
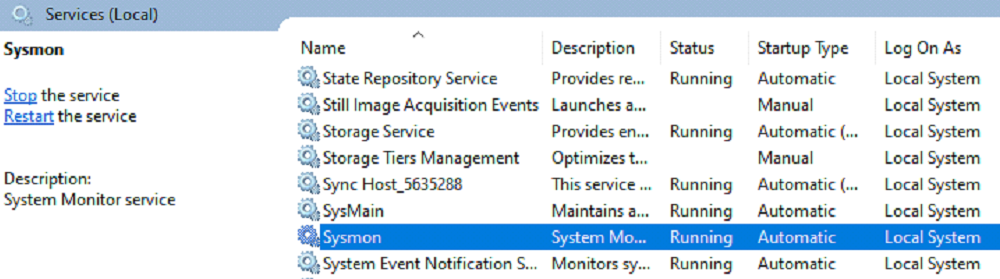
Verify the Service Sysmon start running
Import the configuration file.
Download Link: https://github.com/SwiftOnSecurity/sysmon-config
Command to Import:
sysmon -c sysmonconfig-export.xml
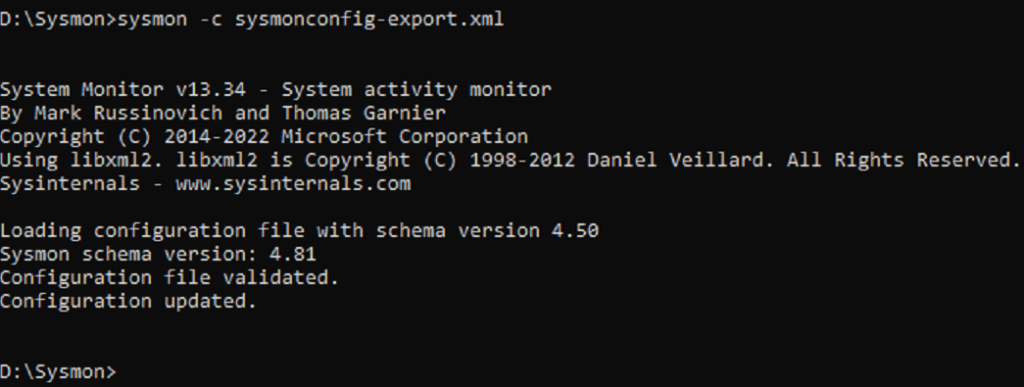
It can create around 25 types of events with lots of information. Moreover, it can also generate error events.

To view the Logs, go to Event Viewer and open the mentioned file.
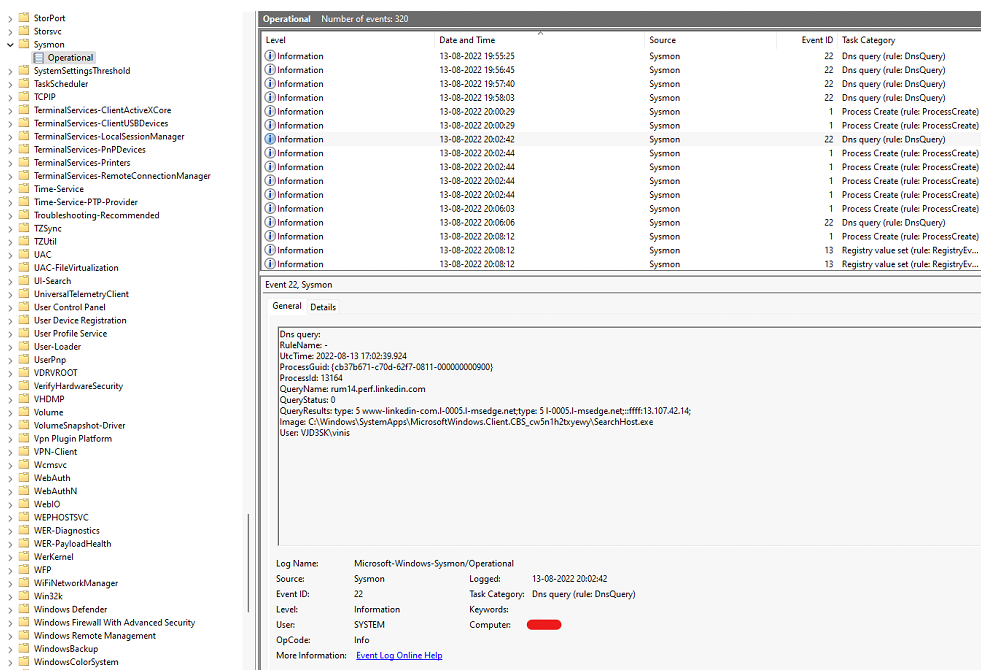
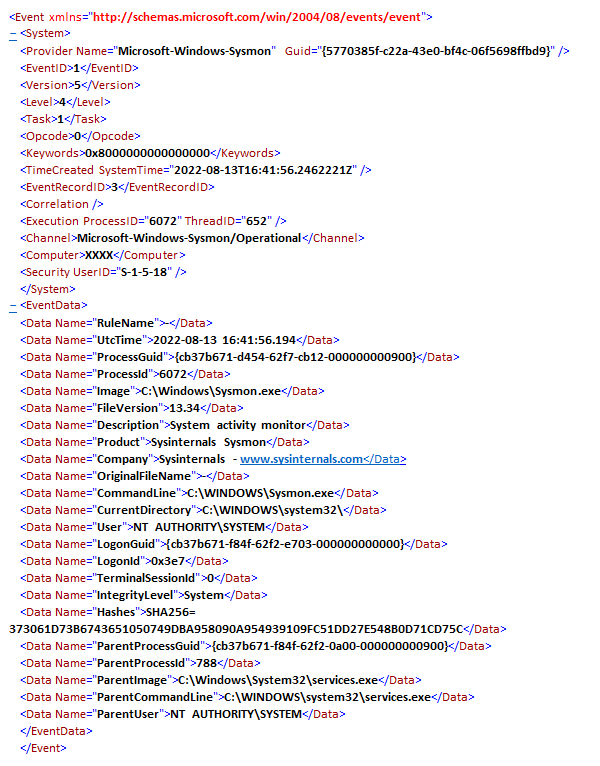
Sample Event:
To Uninstall the Sysmon use the command:
sysmon –u
Installing in Linux also need to follow the same commands. Before that, we need to meet up with Dependencies given in the README.md.
At last Sysmon is one of the best tools. We can protect endpoints using this tool. Lateral movements, C2C and file dropping: all these attacks can be detectable.
However, it has few downsides. Without question, we need to talk about that. Sysmon produces huge volume of logs. Providing storage is the first challenge. Choosing the required events helps to reduce the logs count. In my personal experience, while testing in Servers, a few of the servers, CPU and memory utilizations went high.
MITRE ATT&CK® knowledge base is mostly followed framework. Most of the Attacks from MITRE ATTACK has been covered by the Sysmon. Free of cost and Beast.
Protecting Endpoints are challenging. It has become more crucial after the COVID pandemic. Work from Home has made Cybersecurity more proactive from reactive. Endpoint detection and response (EDR) is providing security for user machines. It helps to protect Files, Web, and Removable media. But acquiring EDR is not easy for all firms. Giant institutions, they…